SolutionOne Blog
Winter is Coming: Dyre Wolf Malware Can Leave Your Bank Account Looking Stark
 With the critically-acclaimed television series, Game of Thrones returning to viewers this spring, it seems apt to discuss a manner of hacking attack called Dyre Wolf. This particular threat is just as fierce as its name implies, and can potentially cost businesses between $500,000 to $1.5 million per attack. It takes advantage of a multi-step phishing process, and your employees should understand how to avoid attacks like these.
With the critically-acclaimed television series, Game of Thrones returning to viewers this spring, it seems apt to discuss a manner of hacking attack called Dyre Wolf. This particular threat is just as fierce as its name implies, and can potentially cost businesses between $500,000 to $1.5 million per attack. It takes advantage of a multi-step phishing process, and your employees should understand how to avoid attacks like these.
The vulnerability was discovered last October, but John Kuhn, a senior threat researcher for IBM, reports that Dyre is following the recent trend of moving toward more sophisticated hacking measures. According to ZDNet, this threat takes advantage of the Dyre banking trojan to infiltrate infrastructures and make off with a hefty chunk of change. They accomplish this by taking advantage of social engineering tactics designed to dupe users into revealing important information about accounts.
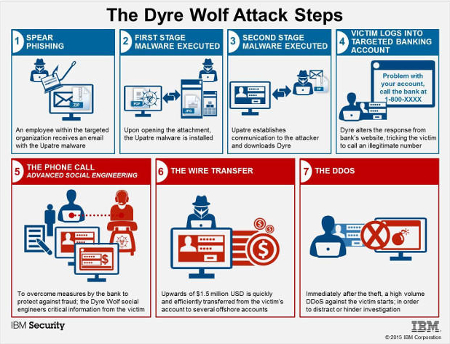
Unlike other Trojans that go after individual bank accounts, Dyre Wolf is designed to tackle large organizations that accrue a lot of profits. This is why it’s important to train your team to identify and manage a phishing attack without falling victim to these social engineering threats. Dyre Wolf uses a seven-step process to pull off these expensive hacks:
- Step 1: Spear Phishing Attacks. The employee will receive a phony email that houses the Upatre malware. This malware is designed to download the Dyre Trojan.
- Step 2: Execution. The Upatre malware installs itself on the computer when opening an infected attachment.
- Step 3: Communication. Upatre downloads Dyre onto the infected system.
- Step 4: Watching and Waiting. Dyre observes the browsing behavior of the infected PC, waiting for the victim to visit one of several hundred banking websites. It then displays a message claiming that there’s an issue with the account, along with a fake support phone number.
- Step 5: The Fake Phone Call. The user calls the fake number and is greeted by a human voice, rather than an automated one. The hacker then proceeds to gather sensitive information and credentials, unbeknownst to the user.
- Step 6: The Wire Transfer. The criminal arranges for the money transfer using the stolen credentials.
- Step 7: DDoS. While the money is being transferred, the targeted organization will experience a distributed denial of service attack. The concept behind this is that the victim’s institution will be too busy dealing with the downtime to realize that they’ve been robbed.
Of course, at the heart of any social engineering hack, the root of the problem comes from employees not understanding how to respond to potential threats. Social engineering thrives off of the average employee not knowing how to counter it; therefore, the best way to take the fight to this new generation of sophisticated hackers is to ingrain best practices into the minds of your workers.
To this end, IBM suggests the following procedures:
- Make sure that employees understand security best practices, and how to report suspicious behavior.
- Perform practice mock exercises to get a feel for how well your employees identify sketchy attachments and email messages. These would be designed to simulate real criminal behavior, and as such, should be an effective means for helping you gather information.
- Offer advanced security training that helps employees understand why they must be on the lookout for suspicious online behavior, and what they can do about it should they encounter it.
- Train employees on how to respond to banking threats, and make sure they know that banks will never request sensitive information that could compromise your account.
These are just a few ways to handle phishing and social engineering scams. For more information on how you can protect your business from these kind of hacks, give SolutionOne a call at (214) 299-8555.
Comments